Running jFTPd as Web Application
To be able to run jFTPd as a Web Application there are several additional steps which must be completed.
Directory for configuration file
jFTPd needs to be able to read an external configuration file (named jftpd.properties). The path to the configuration file is specified via a servlet configuration parameter named configFilePath. After deploying the application, you can edit the jftpd-ws/WEB-INF/web.xml file and update this parameter:
....
<servlet>
<servlet-name>JFTPDServletRunner</servlet-name>
<display-name>JFTPDServletRunner</display-name>
<servlet-class>JFTPDServletRunner</servlet-class>
<init-param>
<param-name>configFilePath</param-name>
<param-value>c:\\opt\\jftpd.properties</param-value>
</init-param>
<load-on-startup>10</load-on-startup>
</servlet>
....
The jftpd.properties file holds informations about the location of users.dat file - as well as locations for the log/debug/error files generated by jFTPd. Asuming that the users.dat file is found in C:\opt directory, a valid configuration file looks like:
logfile=c:\\opt\\ftpd.log
errorlog=c:\\opt\\ftpd.error
debugfile=c:\\opt\\ftpd.debug
debug=true
usersfilename=c:\\opt\\users.dat
timeout=300
Tweaking Tomcat's policy file:
jFTPd needs a policy file to be able to enforce stronger security on what the users are allowed to access on the disk.
When running standalone, the policy file jftpd.security is passed to the JVM using the command line, but now, running from Tomcat, the policies must be added to catalina.policy file [which is the default policy file for Tomcat].
These lines must be added at the end of the catalina.policy file:
grant codeBase "file:${catalina.home}/webapps/jftpd-ws/-" {
permission java.security.SecurityPermission "insertProvider.SunJSSE";
permission java.io.FilePermission "c:\\-", "read, write, delete, execute";
permission java.io.FilePermission "d:\\-", "read, write, delete, execute";
permission java.io.FilePermission "e:\\-", "read, write, delete, execute";
permission java.io.FilePermission "c:\\", "read, write, delete, execute";
permission java.io.FilePermission "d:\\", "read, write, delete, execute";
permission java.io.FilePermission "e:\\", "read, write, delete, execute";
permission java.net.SocketPermission "*", "accept, resolve, listen, connect";
permission java.util.PropertyPermission "user.dir", "read";
permission java.lang.RuntimePermission "loadLibrary.unixruntime";
permission java.util.PropertyPermission "java.execsuffix", "read";
};
Second, Tomcat needs to know about catalina.policy, by adding the
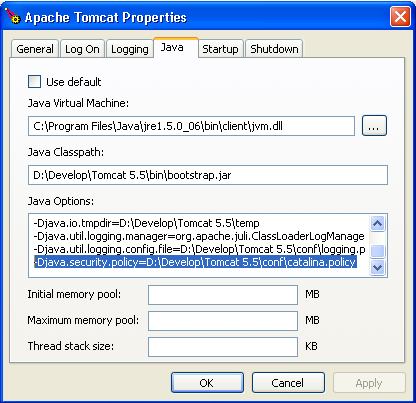
-Djava.security.policy=D:\Develop\Tomcat 5.5\conf\catalina.policy
as argument for Tomcat.
For example, if you run Tomcat from Windows, as Service, you can go to the service properties (using the bin/tomcat5w.exe from Tomcat's directory) and add the line to the Java Options found under the Java tab.
What's NEW?
06/26/2006
Added Tomcat Installation.
06/19/2006
jFTPd Web Page is online!
Create your own web pages in minutes...

Java Secure FTPd Server
Copyright (c) 1999-2001 Prominic Technologies, Inc. and Prominic.RO SRL. All Rights Reserved.